Top 5 RAR Password Crackers/Recovery Software for Window PC
 |
| Top 5 RAR Password Remover/Unlocker |
In this post we learn how to crack/recover RAR file password in Window PC. If you forgot you RAR file password and don’t know how to get it back, read this guide, this is for you.
When you forgot RAR file password, you have two choices. One is ask someone for RAR open password. If unfortunately it doesn’t work, you can reset and remove RAR password with a powerful RAR password Crackers tool.
What is RAR ?
RAR is the format used by WinRAR archiver. The RAR format functions similarly to the ZIP format since they are both data containers. Both of them are also used to compress lots of files. However, as compared to the ZIP format, RAR has more advanced features like the following: more convenient multivolume archives, tight compression, multimedia text modes, AES-128 protection, helping to repair an archive even in case of physical data damage and Unicode support to process non-English file names.
Top 5 RAR Password Crackers/Recovery Software for Windows
1. RAR Password Unlocker
As its name suggests, RAR Password Unlocker, also named as WinRAR password cracker, helps recover lost passwords of RAR files. The program has three ways to retrieve the passwords namely brute-force, brute-force with user-defined mask and dictionary. Moreover, it supports all RAR files created by any program.
Upon opening the program, you have a basic interface with two main choices: RAR Password Recovery and Search Encrypted Files. RAR Password Recovery allows you to open a RAR file that you want to recover the password while Search Encrypted Files scans your entire system to find encrypted files.
Advantages:
The main advantage of the program is its easy-to use user interface.
You won’t have any problem navigating through it. Selecting a RAR file you want to unlock is straightforward.
Disadvantages:
However, while using the RAR Password Unlocker program, there are a couple of crashes. This is a minor problem that could be fixed in the future though.
Also, you need to buy the full version for USD 19.95 to recover more than three-character password.
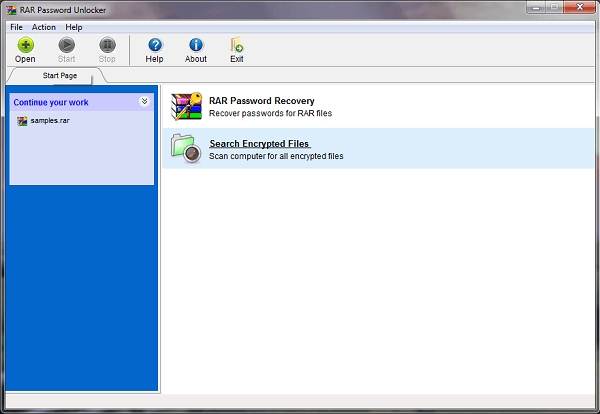 |
| RAR Password Unlocker |
2. KRyLack RAR Password Recovery
KRyLack RAR Password Recovery is a free RAR password cracker tool. It makes use of the brute-force technique in finding the password.
The main screen of the program lets you set all the parameters you want. You can choose a RAR file by clicking on the browse button. It also lets you pick the character sets you think the password contains which makes the recovery process faster. Character sets you can choose are Latin, spaces, digits and symbols. A user-defined character set is also available. Furthermore, you can select the method of recovery by choosing from brute-force, mask and dictionary.
Advantages:
The user interface of the program lays out all the settings in the center of the screen for easy access.
Moreover, the password recovery is pretty quick too. This is because the program allows you to choose certain character sets.
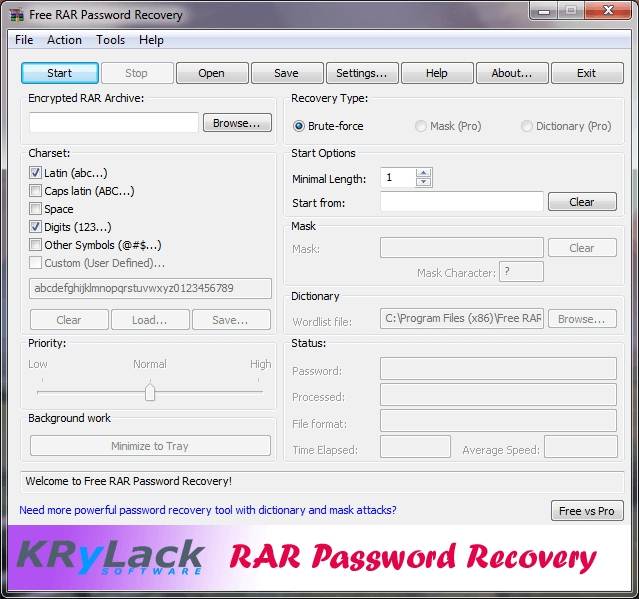 |
| KRyLack RAR Password Recovery |
3. RAR Password Recovery Professional
RAR Password Recovery Professional is password unlocker software. The tool possesses three attack methods: brute-force, brute-force with mask and dictionary. It is optimized for multi-core CPUs and NVIDIA-GPU to recover passwords swiftly.
The interface consists of four tabs namely recovery, brute-force, dictionary and options. To start using the program, click on ‘Open’ to import the password-protected RAR archive. Next, choose from either brute-force or dictionary attack and set up the parameters. Finally, click on ‘Start’ to begin retrieval process.
Advantages:
It is worth mentioning that the application has a beautiful design. Everything is easy to use and pleasing to the eyes.
You can see the progress bar and some information during the recovery process which keeps you updated.
Disadvantages:
The problem with the free version is that it limits the password that can be recovered to three characters only. To get out of this restriction you have to pay USD 19.95.
 |
| RAR Password Recovery Professional |
4. RAR Password Recovery Magic
RAR Password Recovery Magic is a professional tool used for retrieving passwords of RAR archives.
The main interface lets you add encrypted RAR archives by clicking on open button. The settings button has the options for brute force and dictionary. The brute-force mode allows you to select among letters, numbers and symbols, depending on what you think is the password for quicker retrieval. For the dictionary mode, you can select a text file containing the words to be searched.
Advantages:
It has a easy-to-use interface. There are no learning curves when using it for the first time.
Moreover, the tool was able to find out the password of a RAR archive quickly. In just a few minutes, the process is done.
Disadvantages:
Though the free version can only be used ten times, the payment required for the full version is USD 29.99.
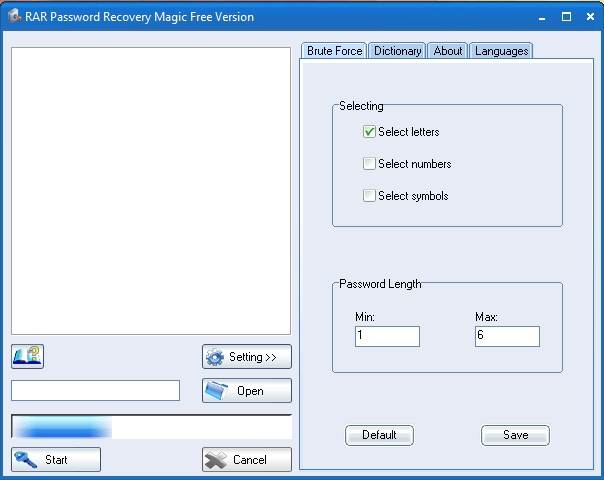 |
| RAR Password Recovery Magic |
5. Daossoft RAR Password Recovery
Daossoft RAR Password Recovery is the answer when you cannot open a RAR file because you forgot the password. It is a program which has the capability of unlocking the password using three attack options. These options are brute-force, brute-force with user-defined mask and dictionary.
Clicking on the open tab allows you to browse and choose RAR files that are password-protected. The application offers a variety of settings like the ability to set ranges for brute force method in order to make the process run faster. For instance, you can select small letters, capital letters, numbers and symbols. Also, you can select the password length. On the other hand, for the dictionary attack, you can choose the file of the dictionary you want to use.
Advantages:
The advantage of using Daossoft RAR Password Recovery is its professional set of features packed in an elegant design.
The application is easy to use as well. There are no problems in finding what you need.
Disadvantages:
A downside of using the tool is it is at times slow to response. It takes some time before the password is cracked.
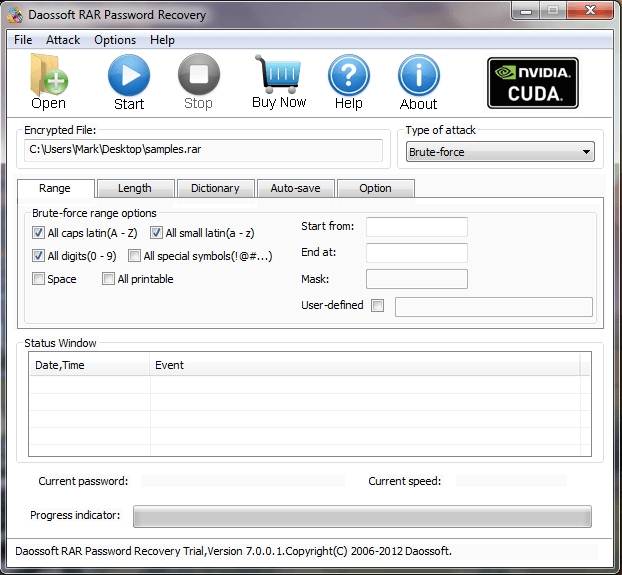 |
| Daossoft RAR Password Recovery |